A new report discusses how volatile networks are being used for Denial of Service (DoS) attacks. Targeted outlets have previously faced censorship and intimidation efforts, including the arrest of employees, physical violence, and online harassment. qurium.org/weaponizing-proxy-and-vpn-providers/volatile-networks/
Entities are leveraging expendable IP networks to launch these attacks, which require access to a large number of IP addresses to bypass detection systems based largely on IP reputation.
Entities involved: Qurium uncovered dozens of "clean networks" being used for DDoS attacks, primarily against entities in Kosovo, Somalia, and Turkmenistan. The attack traffic largely originated from Sprious LLC and involved VPN providers.
Investigations led to IPXO and PhoenixNAP being significant entities enabling such attacks.
Common Denominator: IPXO emerged as the common denominator, leasing networks from a single physical location, routed by SECURED SERVERS LLC (dba PhoenixNAP, CCbill).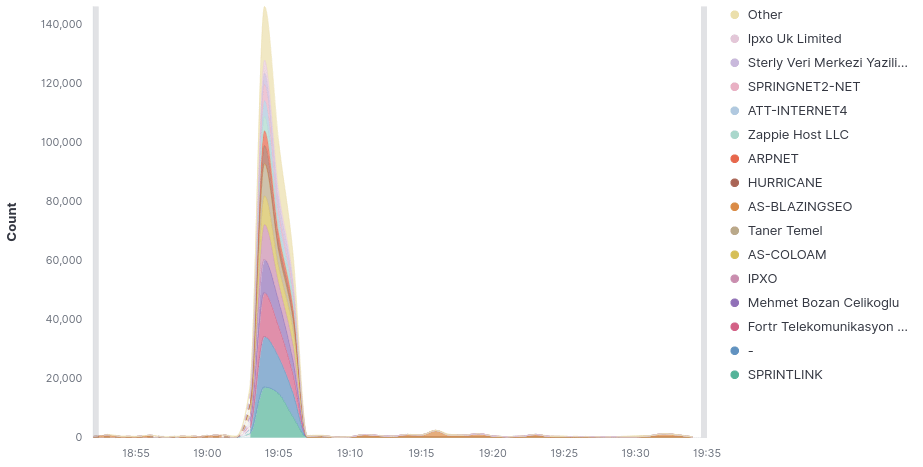
The network prefixes seem to originate from different entities but share a common data center, PhoenixNAP in Ashburn, Virginia.
Attack Methods: Attackers use “volatility of network prefixes," moving them between different upstream providers, active only for a few months, effectively creating a "Bring Your Own IP" DDoS engine.
Attackers leverage IPXO to obtain expendable IPs and announce them from PhoenixNAP to conduct DoS or other forms of attacks, with the real details of the attacker remaining unknown due to non-updating of the WHOIS database.
Lack of Accountability and Action: Despite reporting these activities, IPXO and PhoenixNAP have yet to take significant action against their customers conducting these attacks.
The networks involved in the attacks remain with no customer information, and leasing services have not been terminated, enabling the continued exploitation of these networks for malicious activities.
Ghost Companies: The report reveals how ghost companies, like Aliat LLC, are able to obtain network resources that are weaponized to conduct denial of service attacks.
These networks were leased from IPXO and are still announced from a PhoenixNAP datacenter in Ashburn, USA, with no action taken against them.
twitter.com/Qur1um/status/1701483340006584496?s=20
Victims and Targets: The attacks are primarily focused on media sites, with the network prefixes flooding the victims using more than 75% of the IPs available in the /24 networks, indicating that the networks seem to be fully dedicated to conduct DDoS attacks.
Overall: The investigation reveals a systematic approach to launching DDoS attacks using volatile networks, with entities like IPXO and PhoenixNAP emerging as enablers of such attacks, allowing attackers to exploit expendable and unaccountable IP space.
Despite the knowledge of such activities, there has been a marked lack of remedial action, with networks remaining active and leased services continuing, highlighting critical vulnerabilities and accountability issues in network security and management.