Pleased to unveil this cybersecurity ecosystem map!
After 100+ hrs of meeting w/ experts, I created this deep-dive framework for operators / investors who want to learn about cybersecurity.
I disagree w/ many frameworks used today. We need to go back to basics.
Let's dive in!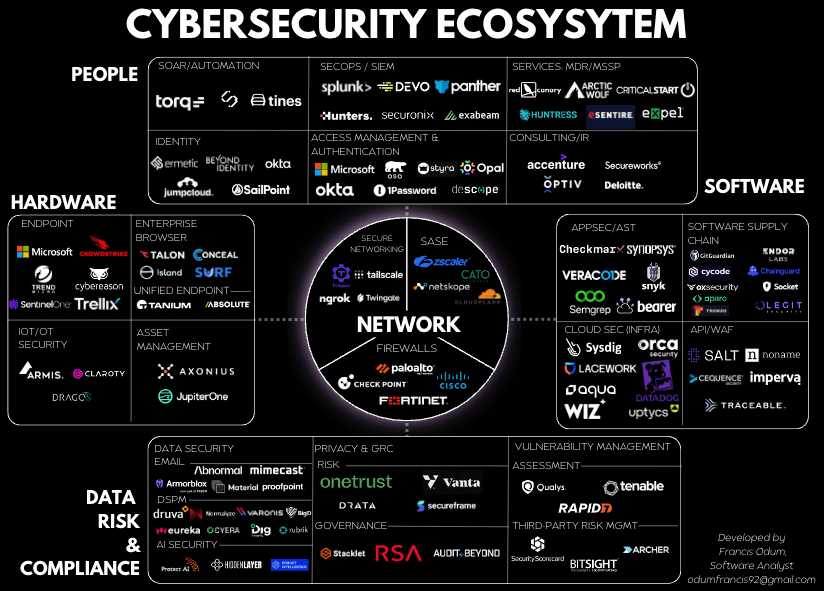
First, some context:
Cybersecurity is a $200B Industry with over 3500+ vendors in 40+ sub-categories w/ TAMs above >$1B!
The pure-play market leader only has a 4% market share, and <10 companies have created >$10B market value!
Making it fragmented / complex for new beginners
However, if we boil things down to basics using first principles, the modern enterprise corporation is made of:
1. People / users
2. Hardware / computers, devices, etc
3. Software / infrastructure / Apps
4. Network / interconnecting point
5. Data / managing risk across 1-4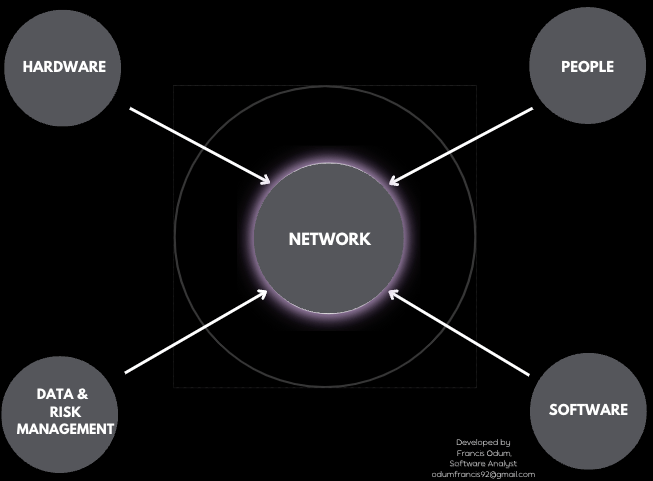
Building upon this foundational layer of the enterprise, Cybersecurity products are layered upon each part!
As attackers find more loopholes within this structure, more cybersecurity solutions / startups are created.
This leads to the current proliferation of point solutions!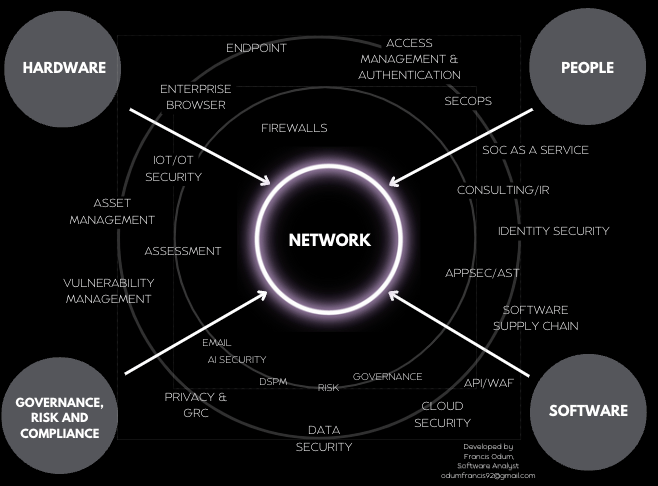
Let's briefly go over each major component!
Network:
The network is the central point and core layer that connects hardware + software + people.
This partly explains why $PANW & $FTNT are some of the largest compounders in security because of their critical role.
Hardware:
Endpoint security is responsible for protecting computers, servers & users against attacks. Modern endpoint studies how users act on these devices.
It's important to note that there are other parts, including IoT/OT security, asset mgmt, and unified endpoint mgmt.
Software:
This category is responsible for protecting the infrastructure (the cloud) and all underlying components that are built on it.
Sub-markets include application security, software supply chain. app security testing, WAF/API security.
More explanation in the deep dive!
People:
These are both users (most vulnerable link) + security protectors!
This category includes:
1) Identity security: Verifying users and their access
2) Internal protectors: Security Operations, & related tools like SIEMs)
3) External advisors: MDR, MSSPs, & consultants
Data & Risk:
How do you manage risk and protect your data across all 4 areas discussed?
This category solves it:
1) Data Security: Includes the sexiest market (GenAI/LLM Security)
2) Governance, Risk & Compliance (GRC): With Gov't playing a bigger role in security, GRC is huge!
To summarize everything, I believe cybersecurity can be boiled down into these five categories despite the current fragmentation and complexity within the industry.
Here is my deep-dive that goes into more depth:
softwareanalyst.substack.com/p/the-beginners-guide-to-cybersecurity
This is a primer / introductory piece for those wanting to expand their security knowledge.
It's a sneak peek into our cybersecurity bootcamp, where we go into more depth covering these categories and companies.
Only 3-days left.
You're welcome to join!
maven.com/saas101live/saasbootcamp
The framework is meant to serve as a guide - hope it's helpful!
Thanks for reading / open to your thoughts!