SASE is the new buzzword in cybersecurity and investing circles, but what is it exactly?
This thread provides a comprehensive breakdown of the evolution of this technology and explains why it will define the next cybersecurity companies:
(FYI - my Twitter is acting up. I posted this thread earlier, but Twitter removed my previous thread, and it all broke up. I've reposted it here for people that bookmarked it.)
If you've reviewed it already, ignore it. Thanks.
Let's start with the basics.
In our homes or if you work at a medium to a large company, you access the internet thru a router.
These routers have a firewall that stays in the middle to protect you + your company against malicious links/websites while accessing the internet.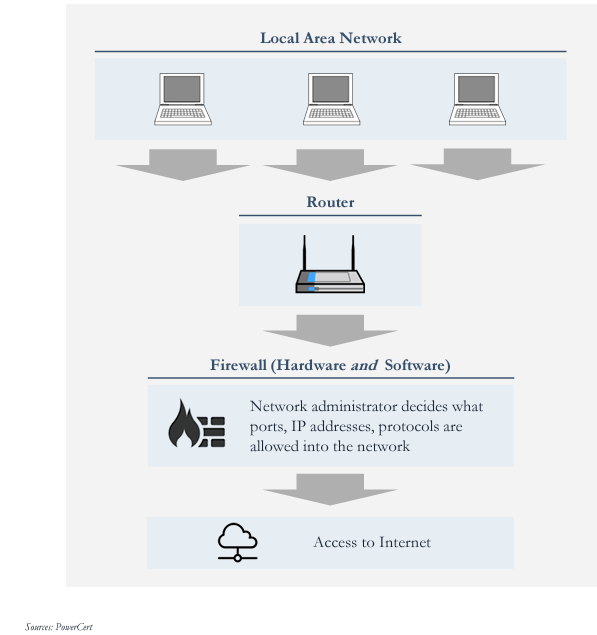
From the 1990s, as the internet evolved w/ the rise of data centers, large cos started using VPNs (see definition below) to serve as a protected way for employees to access the internet.
This became more popular for large cos that had global presence or branch offices (eg banks)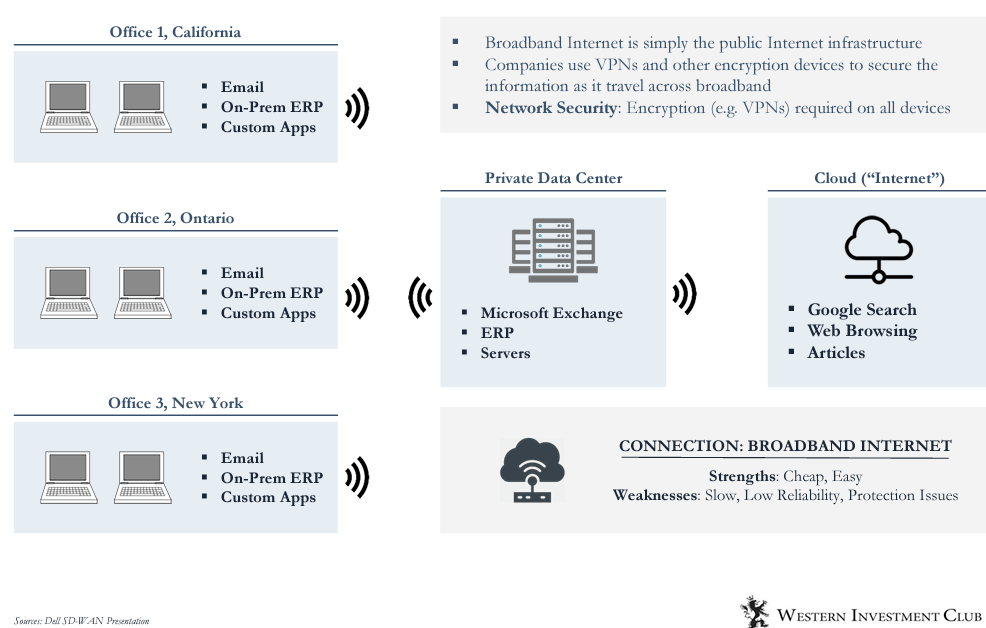
From 2000-2010, companies started to access the internet using an MPLS (Multiprotocol Label Switching) system. See the definitions below.
MPLS is simply a private network to provide company internet w. everything backhauled to a data center with the firewall offering protection.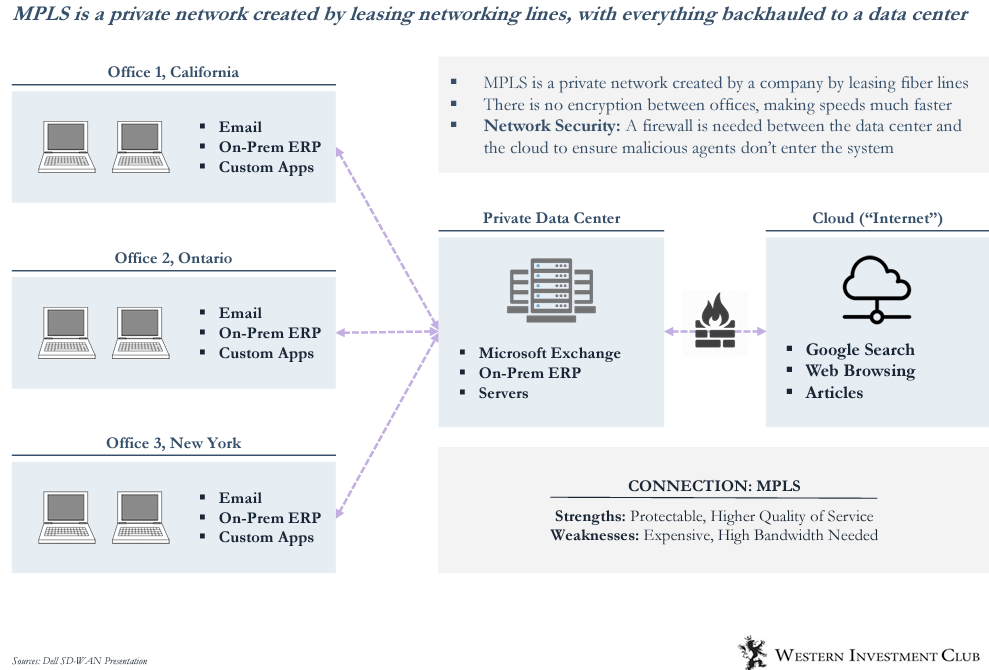
Forward to 2013, w/ the rise of the cloud/SaaS over the last decade.
Many leading companies no longer create new apps or workloads on-prem.
Everything is moving to the cloud, so having physical firewalls to protect data centers makes no sense.
This brings us to SASE:
SASE (Secure Access Service Edge) is the combination of networking (recall: Internet) and security into one cloud platform
It's a framework combining multiple network security features in one, offering visibility into users, traffic, and data when accessing a corporate network.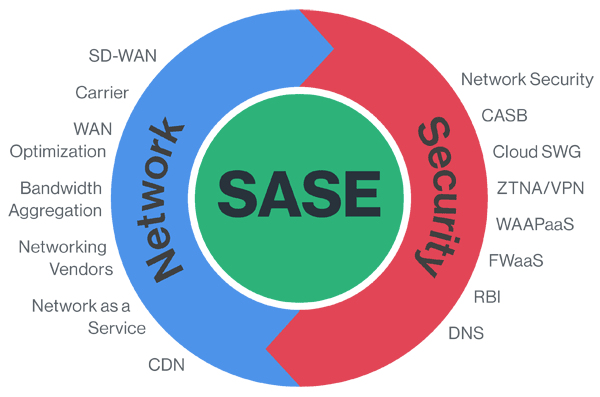
The five CORE features of SASE (As per Gartner before, any company can call itself a SASE provider). They include:
1/ SD-WAN
2/ SWG
3/ CASB
4/ ZTNA
5/ FWaaS (optional IMO)
Goal is to simplify this in easy terms, so I'll use a bodyguard analogy. Here is a written breakdown:
Those five-core features result in the following:
1) CASB -> protects SaaS Apps
2) SWG + FWaaS -> protects your web experience
3) SD-WAN + ZTNA -> protects you while accessing your company's private apps.
The results give you the following below using a sample from Fortinet.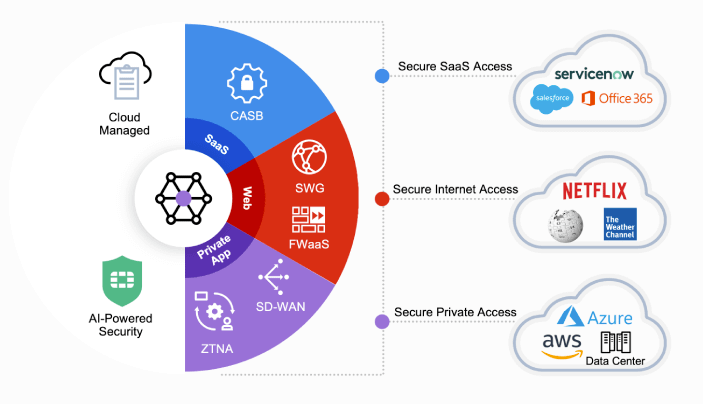
The legacy system was that if you worked in New York but wanted to WFH in Singapore, you'd need to connect to your company's resource on a VPN.
VPN reroutes you back to a data center to verify your identity at the company's HQ, but this is slow and expensive bcos of bandwidth.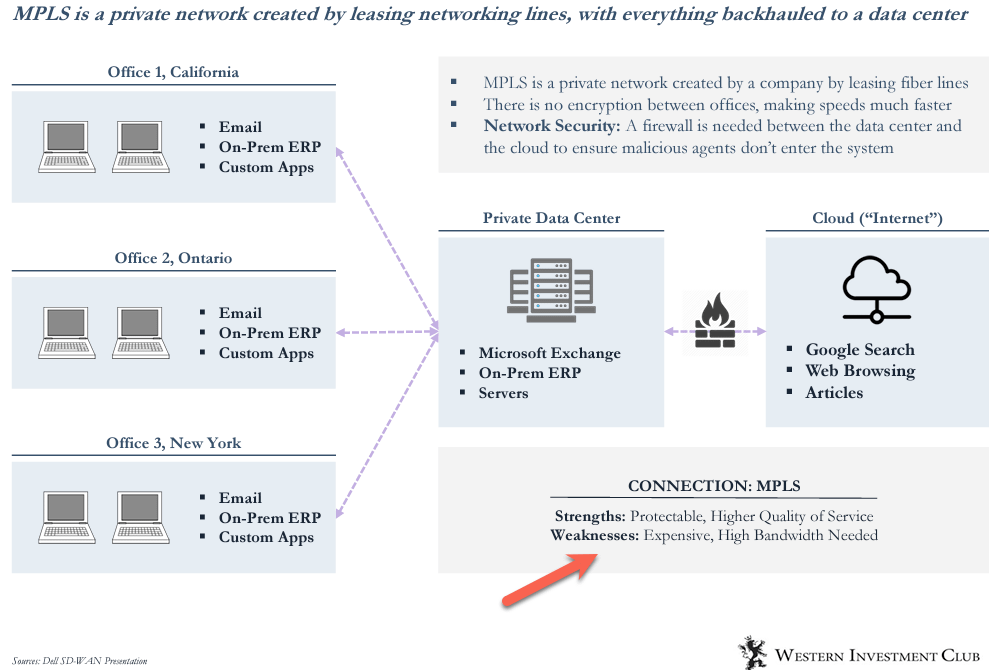
Instead of re-routing you to an HQ data center, SASE allows you to leverage cloud provider + a Telco (like AT&T for Asia) on the edge nearest to you.
The provider acts as an intermediary and verifies you b4 allowing you access to your company's network, enabling faster internet.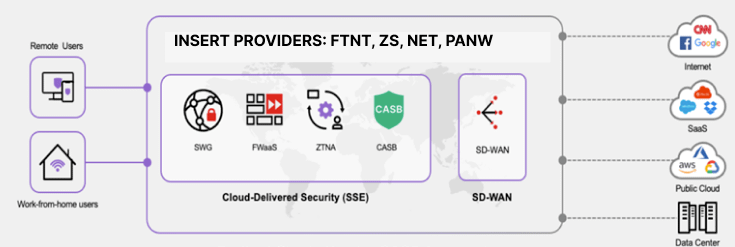
This is the full list of Gartner SASE functions required.
A company must have 13+ products to be called SASE - this gives a glimpse into why only a few cos compete in the space.
As more workloads move to the cloud, SASE is going to be the core architecture for network security.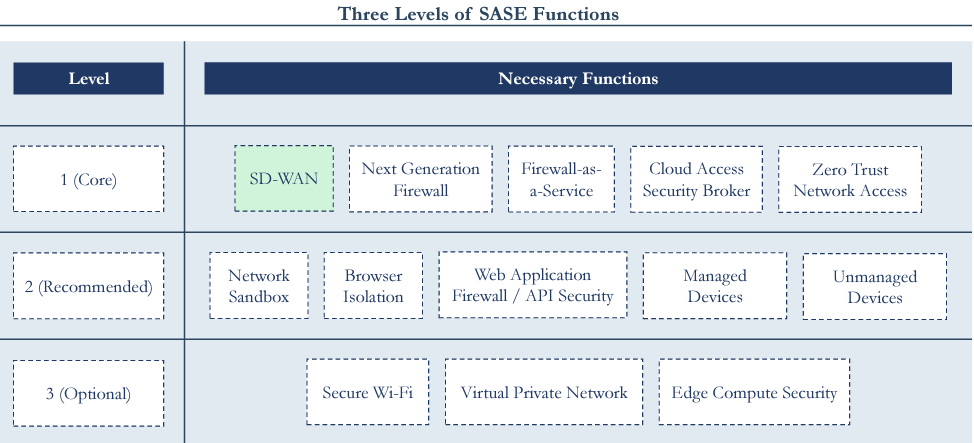
These are the key players based on capabilities IMO:
1) Zscaler
2) PANW
3) Cloudflare
4) Netskope
5) Fortinet
6) Cato Networks
The infrastructure & implementation of SASE is where the companies differentiate themselves.
My next thread covers the competitive landscape.